Releases: guardicore/monkey
Infection Monkey v1.8.2
Infection Monkey 1.8.2
This is a small maintenance release. It includes some bug fixes, some performance improvements, and some new features. To start downloading it while you read the release notes, go to the Infection Monkey website.
New Features 🆕
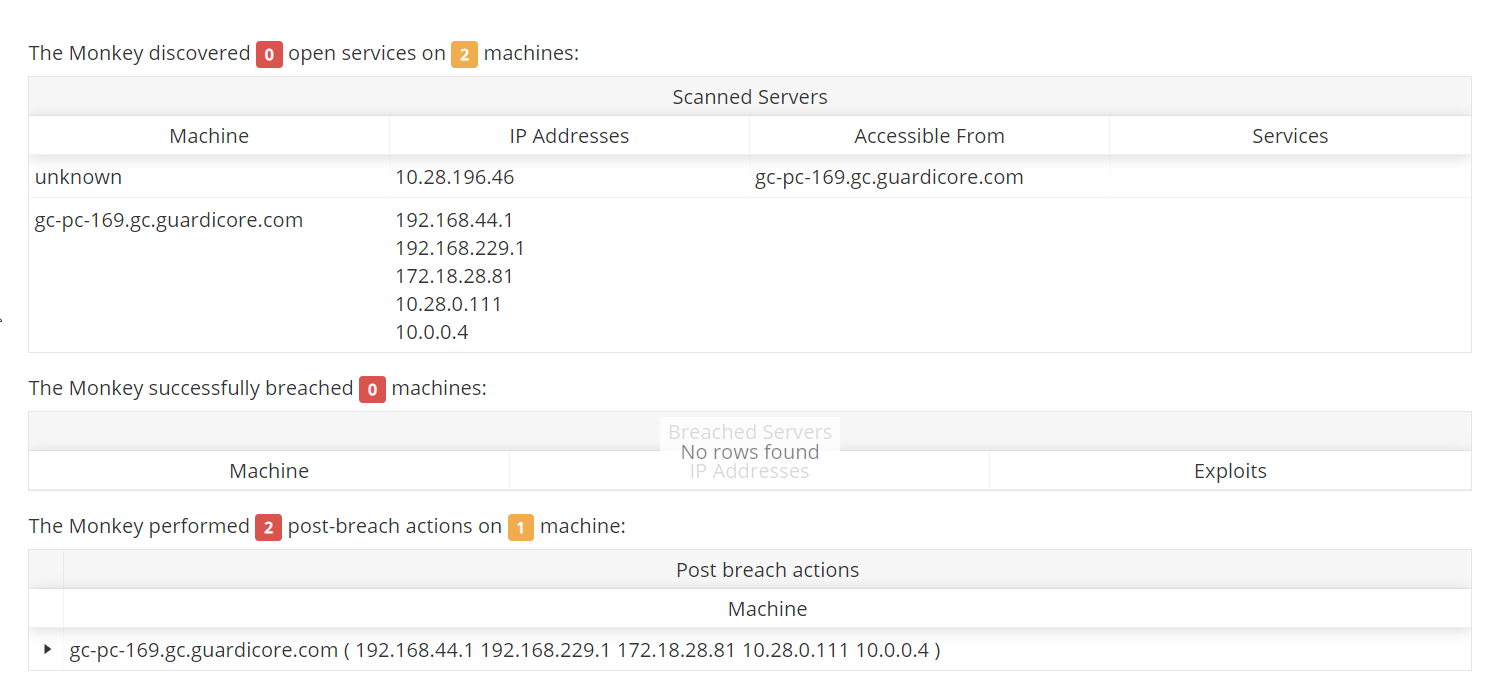
Summary section in Security Report (#635)
Now you can easily see the number of open ports/services and number of servers scanned in the Security Report after a monkey run. Here's how it looks:
Improvements ⤴
Performance improvements 🚤
- Stop exploiting machines that have already been exploited in the exact same manner #650
- UI size improvements and performance improvements #634 #654
- Performance testing infrastructure #632
- Zero Trust report performance improvements #645
Misc.
Bug fixes 🐛
- Fixed monkey ignoring depth restrictions #642
- Fixed UI build issues #643
- Smallfixes on persistance/create user attack technique #647
Attached binaries and hashes:
| Filename | Type | Version | Hash |
|---|---|---|---|
| monkey-linux-32 | agent | 1.8.2 | 39D3FE1C7B33482A8CB9288D323DDE17B539825AB2D736BE66A9582764185478 |
| monkey-linux-64 | agent | 1.8.2 | 4DCE4A115D41B43ADFFC11672FAE2164265F8902267F1355D02BEBB802BD45C5 |
| monkey-windows-32 | agent | 1.8.2 | 86A7D7065E73B795E38F2033BE0C53F3AC808CC67478AED794A7A6C89123979F |
| monkey-windows-64 | agent | 1.8.2 | 2E6A1CB5523D87DDFD48F75B10114617343FBAC8125FA950BA7F00289B38B550 |
Infection Monkey v1.8.0
Infection Monkey 1.8.0
This is a BIG, exciting release, with a ton of new features and improvements. To start downloading it while you read the release notes, go to the Infection Monkey website.
New Features 🆕
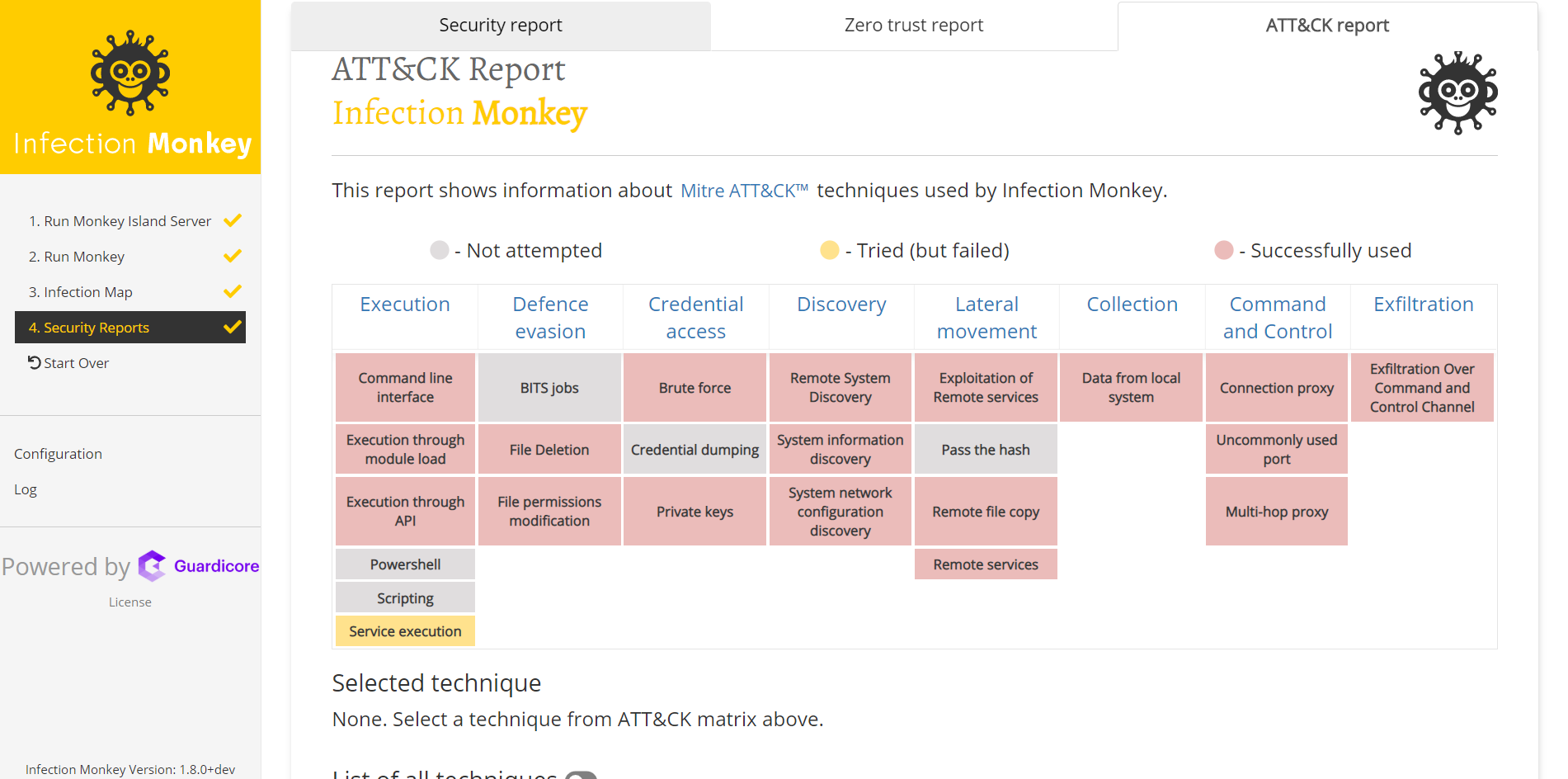
MITRE ATT&CK report (#491, #496, #575, #577)
In the previous version, Infection Monkey started mapping its abilities to the MITRE ATT&CK matrix. We now present these results, alongside the relevant data and mitigations, in a new report that will enable you to understand and mitigate security issues in your network in the vernacular of MITRE.
Here's how it looks:
For more details, read our blog post or watch the overview video.
OS Compatibility (#507, #527, #528, #479, #506)
Since we decided to migrate the Monkey to Python 3.7 🐍, we wanted to make sure that it will still be able to give accurate results on a myriad of operating systems, even old ones that don't support Python 3 at all.
Check out the list of supported operating systems!
This included changes to the Monkey itself and also to us forking our own version of PyInstaller with a custom bootloader.
New Zero Trust People test (#515, #517, #518)
We added another Zero Trust test to the Monkey's arsenal: the Monkey tries to create a new user that communicates with the internet. If it succeeds, this means that the network’s policies were too permissive.
See it in action in this blog post called "How to Assess Your Zero Trust Status: Monkey See, Centra Do".
Improvements ⤴
Python 3 migration (#393, #394, #469, #475, #393, #532, #486, #494)
The Monkey is now Python 3.7! 🐍 🎉 Until the next print VS print() debate creates Python 4, the Monkey is not deprecated.
Improvements to our CI process
Performance testing infrastructure #548 #547
We hope to continue improving our performance as time goes on - this infrastructure will enable automatic testing of performance using Blackbox testing.
Better versioning (#545, #543, #559)
The Monkey version string now has the specific build ID that created it as well. Both the Monkey and the Island log that version string right when booting.
Refactor exploiters, fingerprinters system information collectors (#478, #499, #521, #522, #535)
Now these subsystems are modular and easy to expand using plugins, like PBAs before them (#397).
Telemetry box UI improvements (#538, #565)
The telemetry box in the Map now shows line count and auto-scrolls to the bottom 📜
Small UX QoL improvements
- Config page label explaining that existing monkeys don't get new configuration #525
- "Start over" page now waits for a response from the server #512
Merge Infection Monkey requirements files (#500)
Simplifies our development setup by using only a single requirements file for both Infection Monkey platforms. Thanks pip 🙏
JS File Saver (#473)
Small UI code improvement, less dependencies 👍
New map icons
Bug fixes 🐛
- Blank Screen after inactivity fixed #472
- Added 404 page #501
- Prevention of circular imports #477
- Auto update copyright year #481, #468
- Various fixes to
.debdeployment #533, #544, #503, #524 - Disable
nonefrom the list of networks to scan #550 - Notification wrong route #541
- Improved deploy scripts #549, #562, #564, #546
- Encrypt SSH keys in logs #523, #458
- MSSQL compatibility #492, #493
ringbugfixes #484- Telemetries that don't require briefs no longer throws errors in island #466
New contributors 🙌
Welcome and thanks to our new contributors:
Attached binaries and hashes:
| Filename | Type | Version | Hash |
|---|---|---|---|
| monkey-windows-64.exe | Windows Agent | 1.8.0 | f0bc144ba4ff46094225adaf70d3e92e9aaddb13b59e4e47aa3c2b26fd7d9ad7 |
| monkey-linux-64 | Linux Agent | 1.8.0 | d41314e5df72d5a470974522935c0b03dcb1c1e6b094d4ab700b04d5fec59ae6 |
| monkey-windows-32.exe | Windows Agent | 1.8.0 | 1ddb093f9088a4d4c0af289ff568bbe7a0d057e725e6447055d4fe6c5f4e2c08 |
| monkey-linux-32 | Linux Agent | 1.8.0 | 217cc2b9481f6454fa0a13adf12d9b29ce4e1e6a319971c8db9b446952ce3fb2 |
Infection Monkey v1.7.0
Infection Monkey 1.7.0
This is a BIG, exciting release, with a ton of new features and improvements. To start downloading it while you read the release notes, go to the Infection Monkey website..
New Features 🆕
Zero Trust (#400)
The Monkey now tests your network against the Forrester Zero Trust eXtended framework and provides a report with actionable data and recommendations.
Read more about it in the Infection Monkey for Zero Trust product page or watch a demo video.
MITRE ATT&CK
Adds the ability to configure monkey using the MITRE ATT&CK matrix and allows to view which ATT&CK techniques were used and how in the report.
Improvements ⤴
Scanning Performance boost (#436)
The monkey now scans its target subnets in parallel, which improves runtime by 4.
Island performance boosts (#441 + #358)
The island now generates reports faster for larger amounts of network nodes by 2 orders of magnitude, which helps when dealing with larger-scale networks. Also, the report is cached if no Monkey has communicated since the last report has been generated.
Hashing all sensitive data in all logs (#438 + #444)
All potentially sensitive data is now logged hashed so no sensitive data is plain-text.
Notification when infection is done (#326)
The Island website will now send you a notification when the infection is done, so you don't need to busy wait on it.
Bug fixes 🐛
Various other bug fixes, such as:
- Vulnerability stability and success rate improvements.
- Monkey has TTL before it automatically marked as dead so report finishes in case of lost communication after network changes, shutdowns or crashes. (#313)
- Automatic black-box testing suite. (#420)
- Monkey will work on Windows machines that aren't installed on
C:\. (#349) - Not showing Linux machines in PTH credentials map. (#338)
Attached binaries and hashes:
| File | Hash (SHA256) |
|---|---|
| monkey-linux-32 | EF7A72FFDDF3A54C74F458201A45B51B779A68C460A309B0D5FD247264D7137D |
| monkey-linux-64 | 333529B3061473BF5EE713FA7E3DF4B05DD01823840BB92E1E715488A749B9EA |
| monkey-windows-32.exe | 603D982D4A3D8459573D016E36BCFC0AD776CE2CB7DFF965954C688AB17E1727 |
| monkey-windows-64.exe | E400F0D56570215C458D6EDED63E72AC6E82819EFF2FC5969A73883261B5976E |
Infection Monkey 1.6.3
This is a small bugfix release, mostly around integration and packaging.
Two user facing changes.
First, we now do not request AWS access keys for different features like AWS security hub integration and remote commands on EC2 instances. We now require an IAM role to be applied to the EC2 instance where the monkey is running. For more details, check here and here
Second, the Monkey Island now checks for updates against a centralized server. At startup, a single message containing the current version is sent to a dedicated machine, and returns whether there is a new version available and a download link in case there is one.
Feature - Version checking #309
Feature - AWS integration through IAM roles #281
Bugfix - Deb does not rely on package manager mongo #301
Bugfix - ElasticGroovy exploitation now gracefully timeouts in case of errors #289
Bugfix - Struts2 attack script does not check for certificate errors #318
Bugfix - Domain related recommendations do not show up if no such recommendations exist. #278 and #304 fixes #213
Bugfix - Update Bootstrap to 3.4.1 #311
Also, the Island may now also run as a single PyInstaller packed executable, solving some deployment issues on Windows.
Infection Monkey 1.6.2
This is a release with plenty of cool features.
Take the Infection Monkey for a spin inside your network and let us know how it was!
New Features
- The UI can now optionally be password protected. For more information check our wiki and #260
- The Monkey can now run actions after breaching the machine. For now, we've only implemented the option to create a disabled backdoor user. #242
- Export to AWS security hub. The monkey now knows to export security findings to the AWS security hub. #221
- We can now remotely run commands on AWS EC2 instances, giving you more methods to start a simulating breach. #259
- Attack according to host names rather than IPs #189
- We can now carry our own version of traceroute for linux machines #229
- Add option to sleep between scans #240
- The monkey now also pings machines to check if they're alive, possibly bypassing some segmentation rules #243
- We have an experimental new attack. An MS-SQL exploiter that brute forces authentication and uses xp_cmdshell to attack. #147
We also improved our deployment, making it easier for developers to set up their own instance of the Monkey (#225 and #227 )
Fixes
Infection Monkey 1.6
A whole bunch of new features.
Take the Infection Monkey for a spin inside your network and let us know how it was!
New Features:
Detect cross segment traffic! The Monkey can now easily test whether two network segments are properly separated. PR #120.
The Monkey can analyse your domain for possible Pass the Hash attacks. By cross referencing information collected by Mimikatz, the Monkey can now detect usage of identical passwords, cached logins with access to critical servers and more. #170
SSH key stealing. The monkey will now steal accessible SSH keys and use them when connecting to SSH servers, PR #138.
Implement a cross platform attack for Struts2 Multi-part file upload vulnerability, PR #179.
Implement a cross platform attack for Oracle Web Logic CVE-2017-10271, PR #180.
ElasticGroovy attack now supports Windows victims, PR #181.
Hadoop cluster RCE - Abuse unauthenticated access to YARN resource manager, PR #182.
Code improvements
-- We've refactored the codebase, so now it's easier to share code between the Monkey and the Monkey Island components. PR #145.
-- Mimikatz is now bundled into a password protected ZIP file and extracted only if required. Makes deployment easier with AV software. PR #169.
-- Monkey Island now properly logs itself to a file and console. So if you got bugs, it'll now be easier to figure them out. PR #139.
-- Systemd permissions are now properly locked down
-- Fixed a situation where a successful shellshock attack could freeze the attacking Monkey. #200
We also now have a basic dockerfile available if you want to wrap up the Monkey into a container straight from Github
Infection Monkey 1.5.2
This is another incremental release, with the following changelist
New feature - Azure password harvesting. Detect Azure credentials at risk and the test the impact of harvesting these passwords. See #110
New feature - Improved UI for listing IPs to attack, now supports listing subnets in CIDR format or 192.168.1.30-192.168.1.40 . See #94
Bugfixes
-- Fixed spurious victim discovery. Issue #108
-- 32bit Monkey installed on a 64bit windows machine will now upgrade itself itself to a 64-bit monkey version. See #104
-- Fixed encoding issues when handling unicode password credentials. See #112
-- Fixed incorrect deployment documentation
-- Fixed edge cases in ElasticGroovy attack module
Infection Monkey 1.5.1
This is a small release, one new feature and a few bugfixes.
- New feature - Azure password harvesting. If running on an Azure VM, the Monkey will attempt to harvest password credentials used the VM Access plugin.
- Bugfixes
-- Fixed spurious victim discovery
-- Fix a missing python dependency in the Infection Monkey itself
-- Fixed edge case in the ElasticSearch attack
-- Fixed bugs in handling configuration variables in the Monkey
Thanks to everyone who reported bugs.
v1.5
This version of the Infection Monkey contains
- New UI with a better map display and easier configuration
- A reporting feature with analysis of the Monkey run
- New exploits such as Sambacry and ElasticSearch pre-auth vulnerability
- Pass the Hash attacks when attacking Windows machines
- Bundled Mimikatz
You can read more in our release post
https://groups.google.com/forum/#!topic/infection-monkey/xnzvtxCknt4